搜索结果: 1-15 共查到“Protocols”相关记录406条 . 查询时间(0.118 秒)
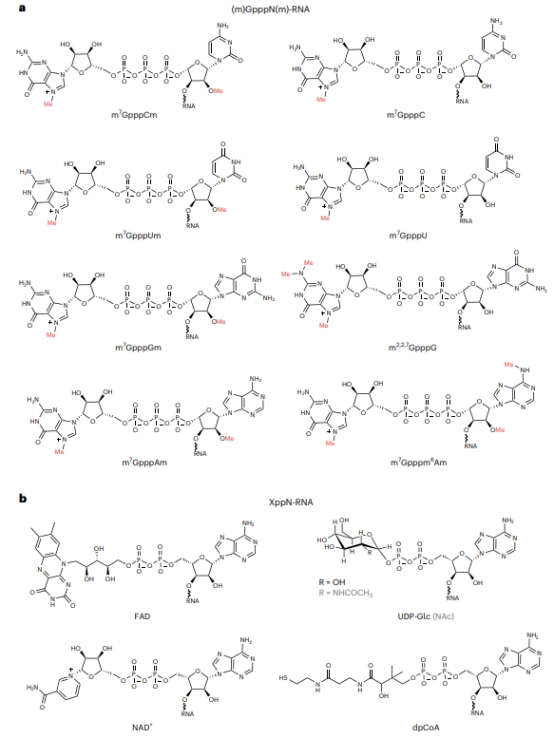
内蒙古大学王进研究员团队在Nature Protocols发表RNA端帽表观转录组系统级分析新技术的详细方法流程(图)
内蒙古大学 王进 Nature Protocols RNA端帽 表观转录组
2023/12/2
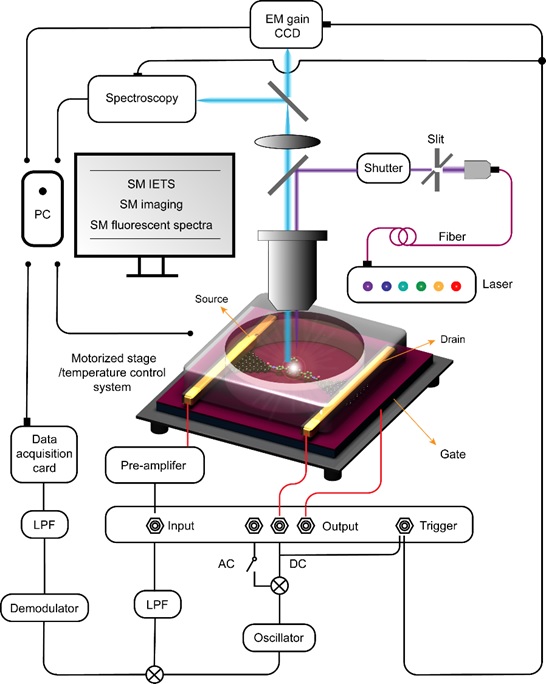
Nature Protocols: 郭雪峰教授教你制备单分子芯片(图)
郭雪峰 单分子 多功能分子器
2023/6/20

2023年2月3日,华中科技大学光学与电子信息学院费鹏团队在Cell子刊STAR Protocols杂志上发表了题为“A practical guide to deep-learning light-field microscopy for 3D imaging of biological dynamics”的实验方案文章。该文章提供了深度学习增强光场显微镜的实施步骤,其中包括简单易实施的光场显微...
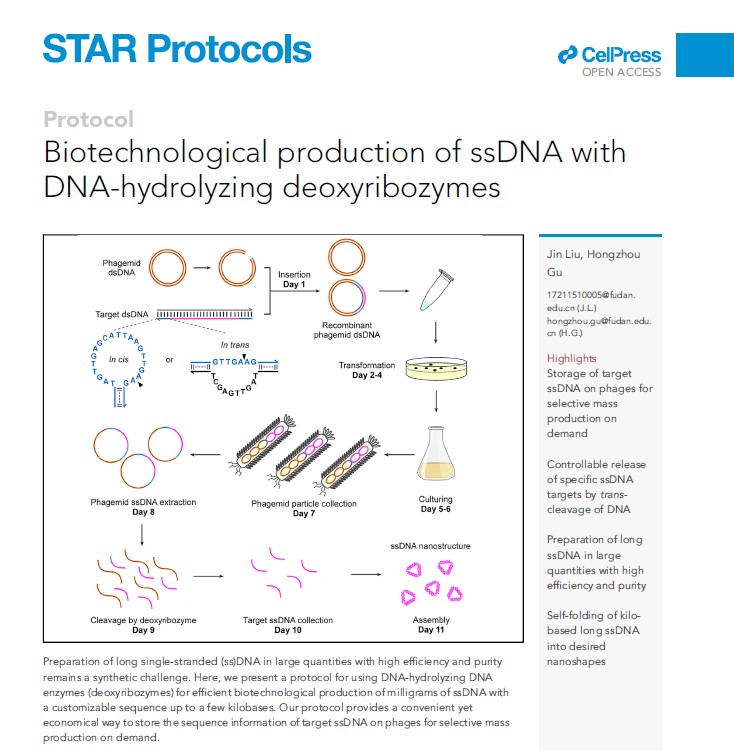
当前,单链DNA序列的体外获取严重依赖于固相化学合成,其技术上已非常成熟,但依然具有明显的局限性。比如,化学合成DNA的产率随着序列长度的增加而显著降低,当超过200个碱基时,化学合成得到的DNA不仅产率/量低下,而且成本较高。换言之,化学合成长单链DNA的性价比很低,该缺点严重限制了很多基于长单链DNA序列的下游生物技术的应用,如长单链DNA模板介导的基因敲入、基于长单链DNA锁式探针的长程测序...

2021年1月13日,浙江大学生命科学研究院蒋超研究员在Nature Protocols上在线发表题为:“Decoding personal biotic and abiotic airborne exposome”的方法学文章。该文章从设备开发、试验流程以及生信分析角度系统的描述了揭秘个体水平空气暴露组组分的研究方法。

四川大学华西口腔医学院林云锋团队在Nature Protocols发表文章——阐述以DNA四面体纳米材料为载体的功能性运载系统及其在医学领域中的应用(图)
林云锋 DNA四面体 纳米材料 功能性 运载系统 医学领域
2020/9/18
近日,我校华西口腔医学院、生物医学工程学院的林云锋教授团队,在国际前沿期刊《NatureProtocols》上发表了题为“Design, fabrication and applications oftetrahedral DNA nanostructure-based multifunctional complexes in drug deliveryand biomedical treatme...
On inverse protocols of Post Quantum Cryptography based on pairs of noncommutative multivariate platforms used in tandem
Multivariate Cryptography Noncommutative Cryptography stable transformation groups and semigroups
2019/8/6
Non-commutative cryptography studies cryptographic primitives and systems which are based on algebraic structures like groups, semigroups and noncommutative rings. We con-tinue to investigate inverse ...
On Designing Lightweight RFID Protocols for Medical IoT
RFID Authentication Ultralightweight
2019/7/23
Recently, in IEEE Transactions on Industrial Informatics, Fan et al. proposed a lightweight RFID protocol which has been suggested to be employed for protecting the Medical Privacy in an IoT system. H...
Seems Legit: Automated Analysis of Subtle Attacks on Protocols that Use Signatures
signature schemes symbolic models formal methods
2019/7/10
The standard definition of security for digital signatures---existential unforgeability---does not ensure certain properties that protocol designers might expect. For example, in many modern signature...
A Round-Collapse Theorem for Computationally-Sound Protocols; or, TFNP is Hard (on Average) in Pessiland
TFNP round-collapse average-case hardness
2019/6/26
This result follows from a more general theory of interactive average-case complexity, and in particular, a novel round-collapse theorem for computationally-sound protocols, analogous to Babai-Moran's...
Highly Efficient Key Exchange Protocols with Optimal Tightness -- Enabling real-world deployments with theoretically sound parameters
AKE provable security tightness
2019/6/24
In this paper we give nearly-tight reductions for modern implicitly authenticated Diffie-Hellman protocols in the style of the Signal and Noise protocols which are extremely simple and efficient. Unli...
On Deploying Secure Computing Commercially: Private Intersection-Sum Protocols and their Business Applications
secure computation private intersection-sum secure aggregate ad conversion
2019/6/19
In this work, we describe how to deploy a cryptographic secure computation protocol for routine use in industry. Based on our experience, we identify major preliminaries and enabling factors which we ...
On sigma protocols with helper for MQ and PKP, fishy signature schemes and more
zero knowledge Post-Quantum digital signatures Multivariate cryptography
2019/5/21
We then remove the helper from the protocol with a "cut-and-choose" protocol and we apply the Fiat-Shamir transform to obtain signature schemes with security proof in the QROM. We show that the result...
Prime, Order Please! Revisiting Small Subgroup and Invalid Curve Attacks on Protocols using Diffie-Hellman
formal verification symbolic model tamarin prover
2019/5/21
Diffie-Hellman groups are a widely used component in cryptographic protocols in which a shared secret is needed. These protocols are typically proven to be secure under the assumption they are impleme...
Efficient Symmetric Primitives for Advanced Cryptographic Protocols (A Marvellous Contribution)
Vision Rescue Marvellous
2019/4/28
While common symmetric primitives like the AES and SHA3 are optimized for efficient hardware and software implementations, a range of emerging applications using advanced cryptographic protocols such ...


